- Prevents Fake Websites: DNSSEC makes it much harder for attackers to poison the cache and redirect users to fake websites.
- Protects Your Information: By reaching the real website, you're less likely to have your personal information stolen by imposters.
- Safer Online Experience: DNSSEC helps to create a more secure online environment for everyone.
- Brand Protection: There is a risk that a person who wants to reach your website with your domain may end up on a fake website.
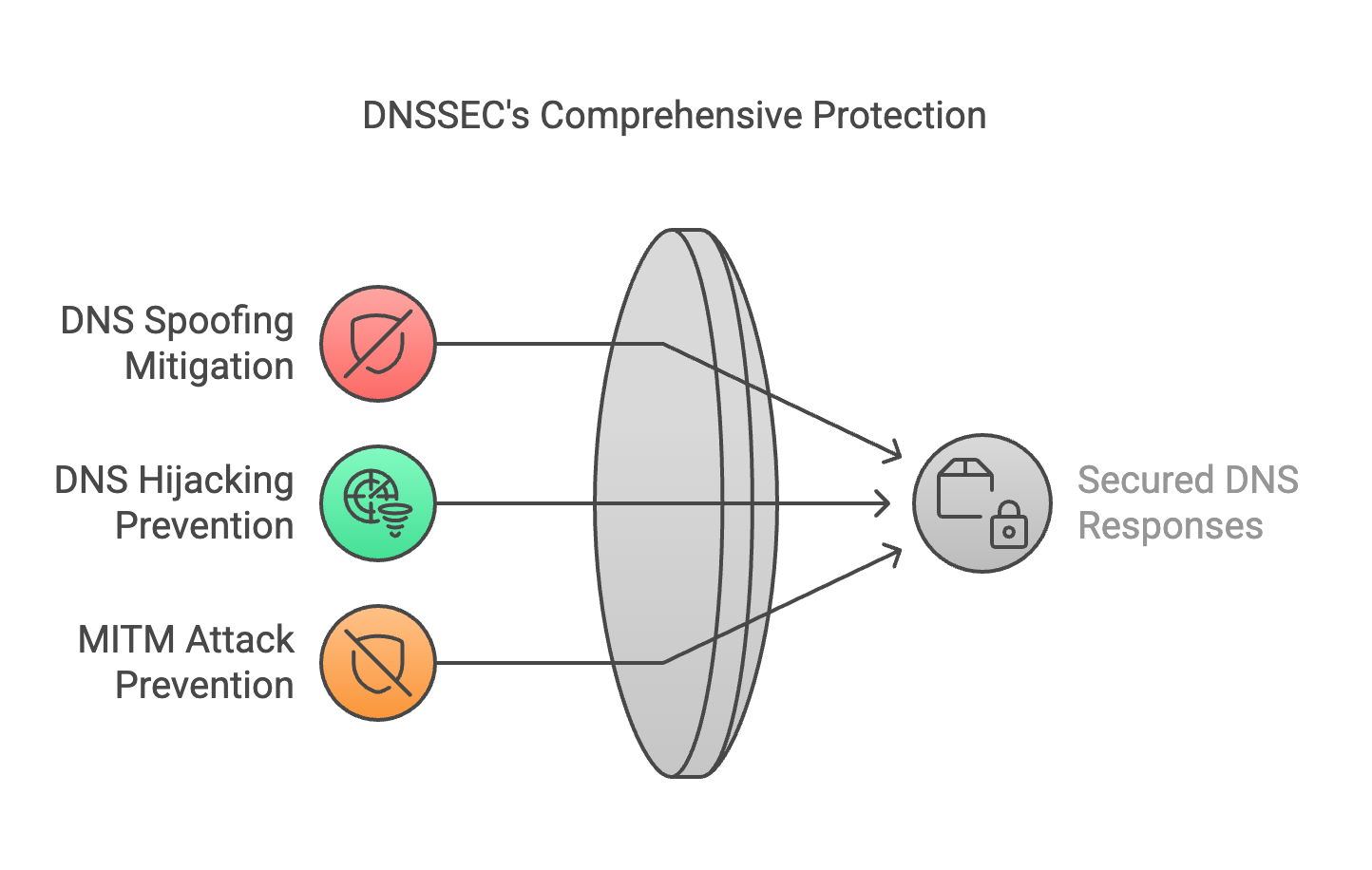
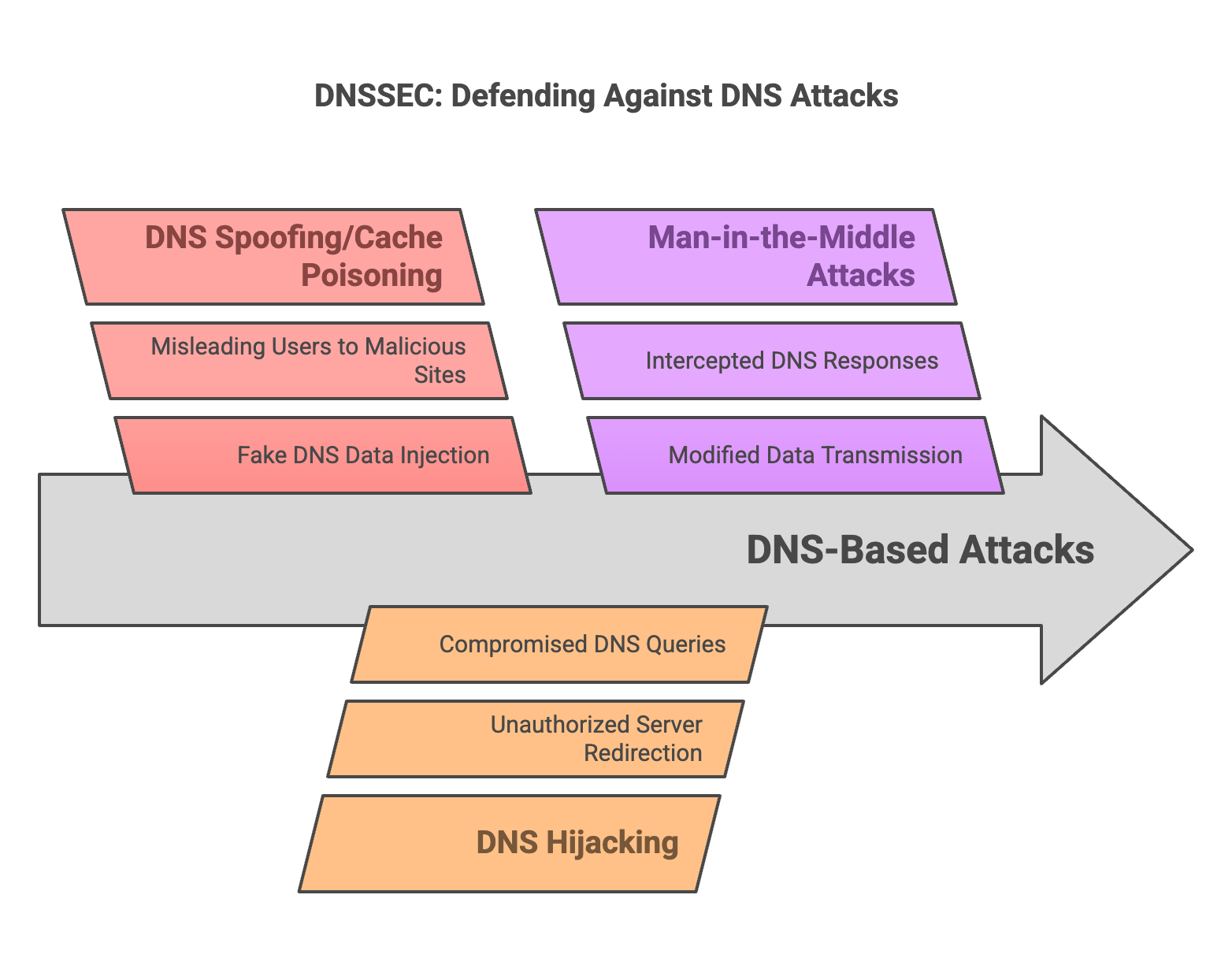
What Attacks Does DNSSEC Mitigate?
DNSSEC (Domain Name System Security Extensions) helps prevent various DNS-based attacks. Some of the key threats it mitigates include:
- DNS Spoofing/Cache Poisoning: Attackers inject fake DNS data into a resolver’s cache, misleading users to malicious sites. DNSSEC uses cryptographic signatures to validate DNS responses, making this attack ineffective.
- DNS Hijacking: This attack redirects DNS queries to an unauthorized server. DNSSEC ensures the authenticity of DNS responses, preventing unauthorized redirection.
- Man-in-the-Middle (MITM) Attacks: Attackers intercept and modify DNS responses. DNSSEC ensures that responses are signed and verified, preventing tampering.
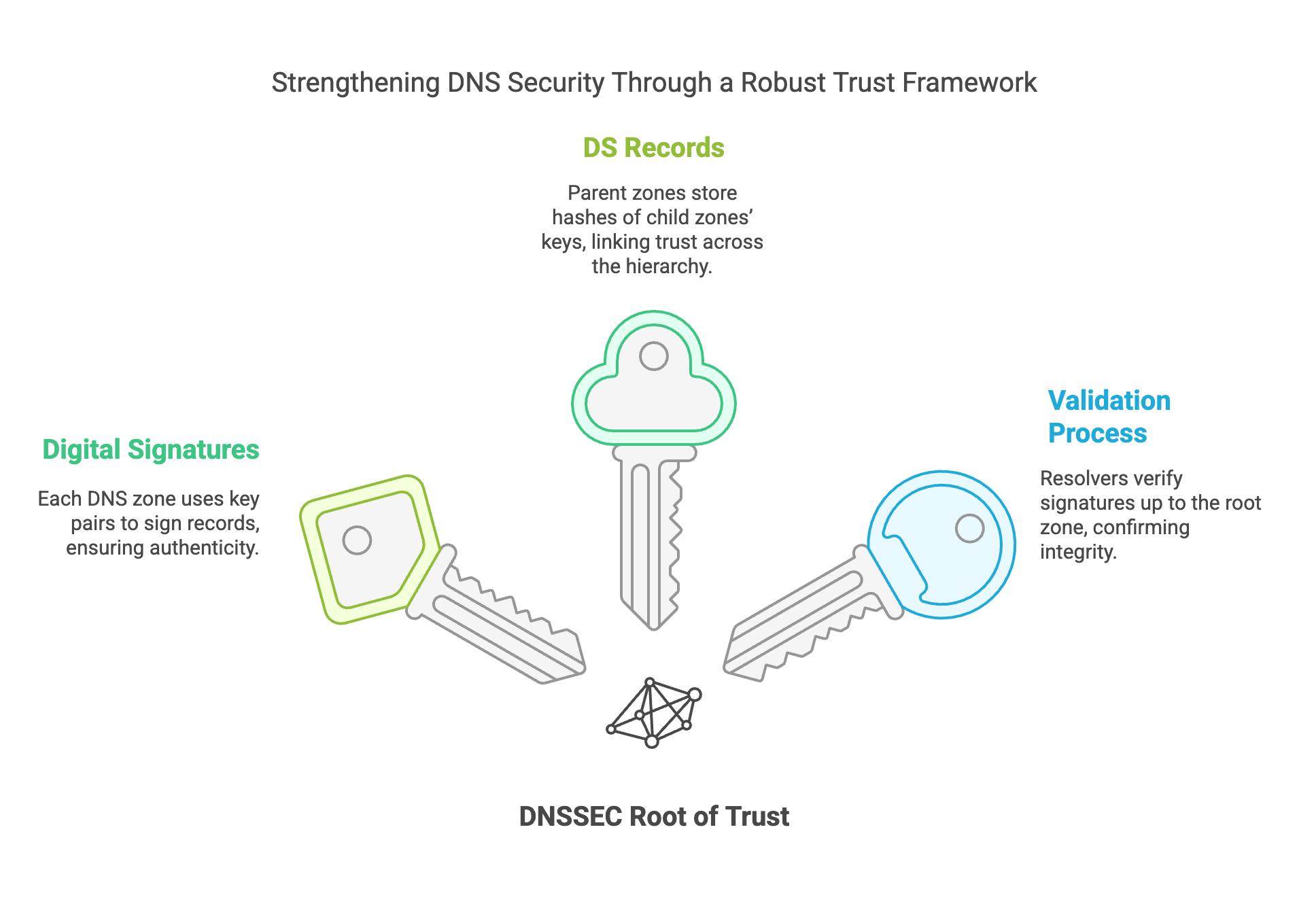
What is the Chain of Trust in DNSSEC?
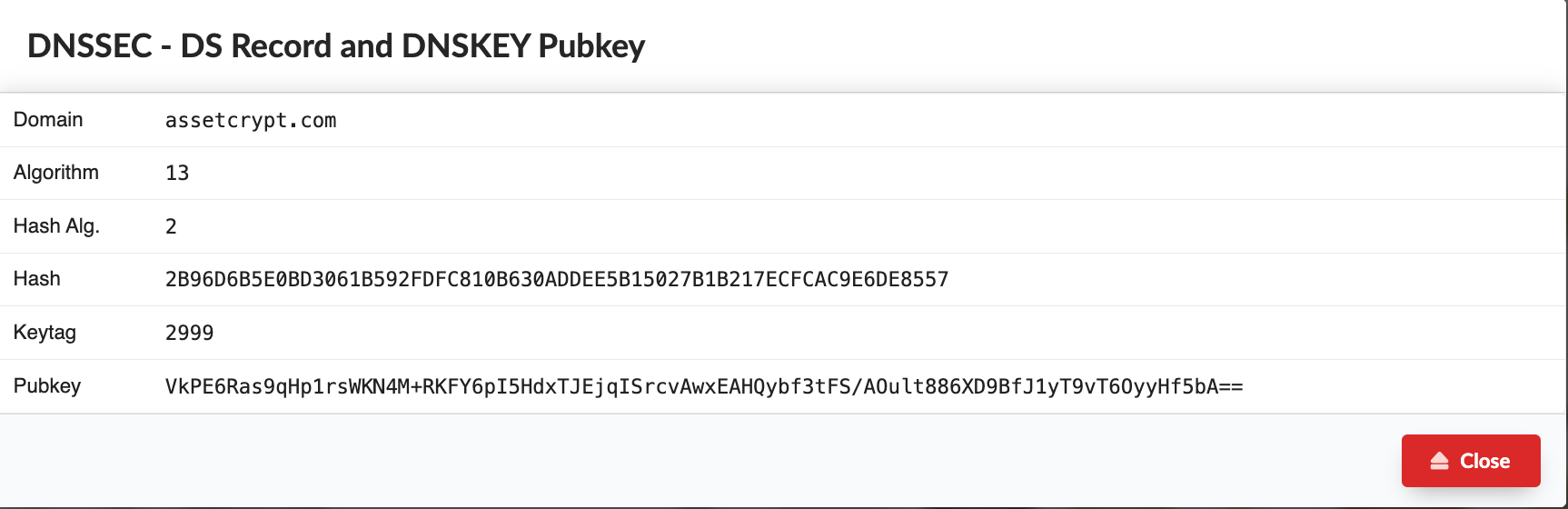
DNSSEC uses a hierarchical "Chain of Trust" to ensure that DNS records are authentic and untampered. It involves:
- Digital Signatures: Each DNS zone has a key pair, and the zone signs its records to prove authenticity.
- Delegation Signer (DS) Records: Parent zones store hashes of child zones’ keys, linking trust across the DNS hierarchy.
- Validation Process: When a resolver queries a domain, it verifies digital signatures up to the root zone.
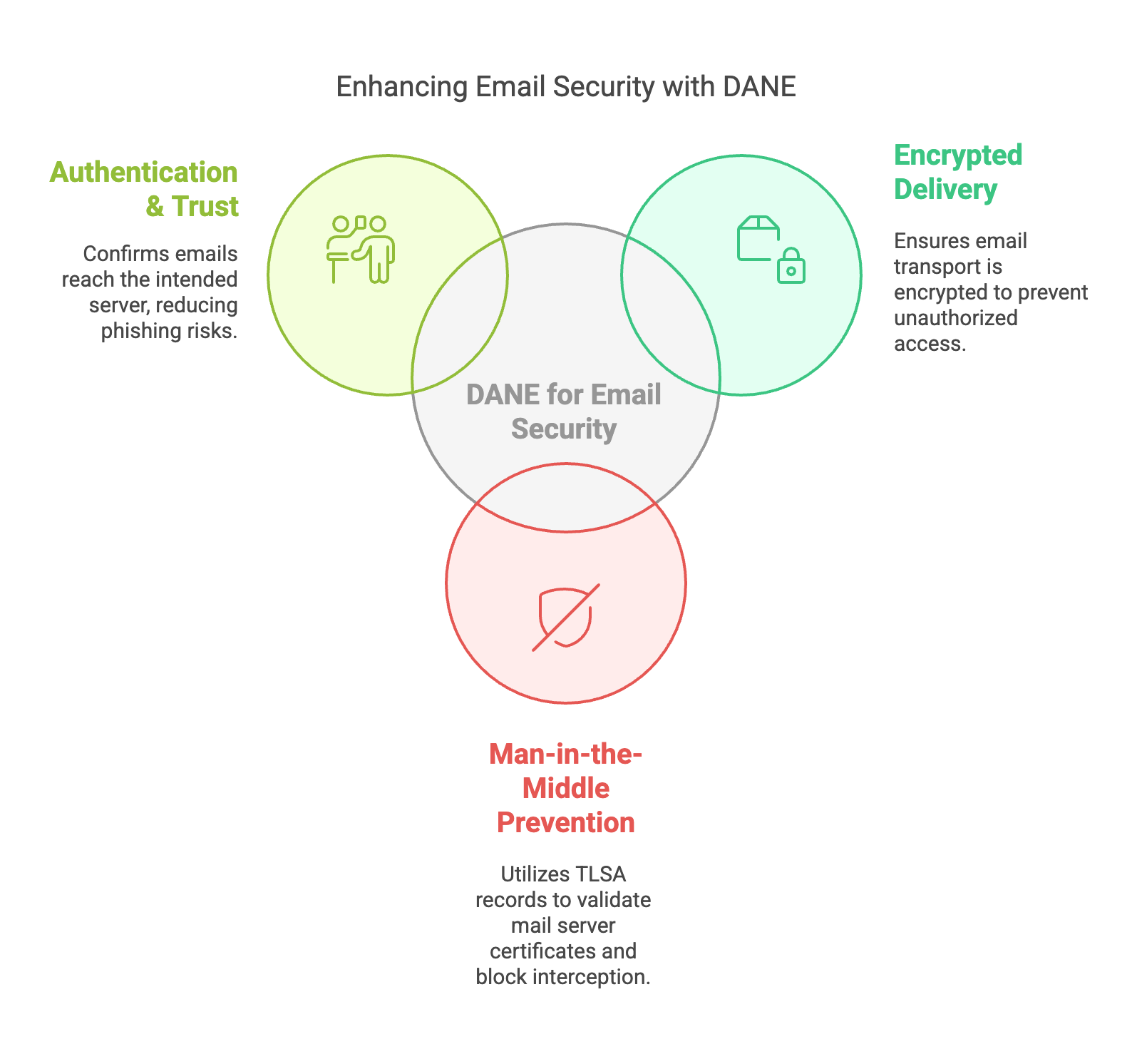
DANE for Email Security
DANE (DNS-Based Authentication of Named Entities) enhances email security by ensuring TLS encryption is enforced and validated through DNSSEC.
- Encrypted Email Delivery: Ensures that email transport is encrypted and prevents downgrade attacks.
- Prevents Man-in-the-Middle Attacks: Uses TLSA records in DNSSEC to validate mail server certificates.
- Authentication & Trust: Confirms that emails are delivered to the intended server, reducing the risk of phishing and interception.
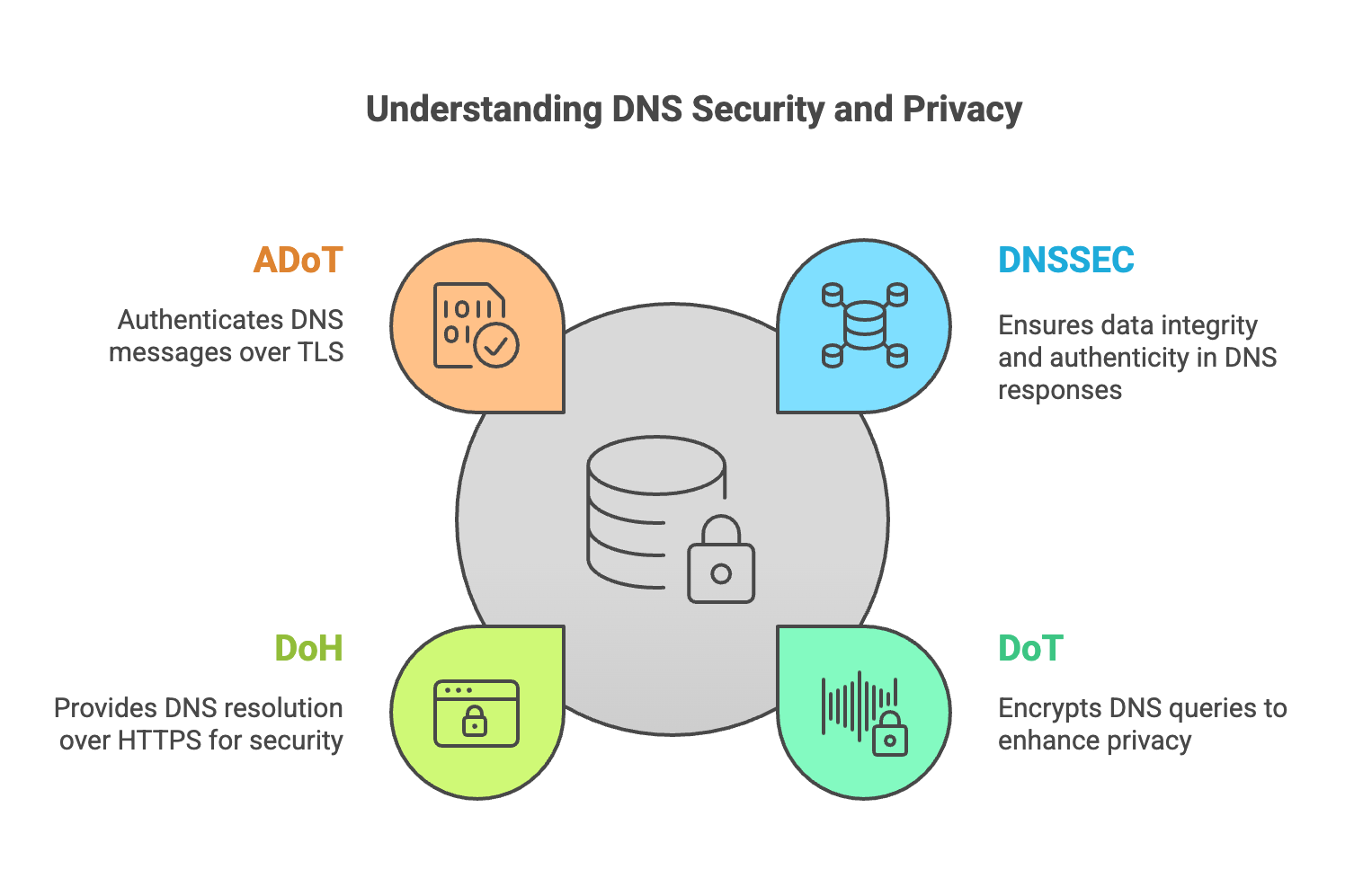
What Are DoT, DoH, and ADoT?
DNSSEC primarily ensures data integrity, but it does not provide encryption. This is where DoT, DoH, and ADoT come into play.
DNS over TLS (DoT)
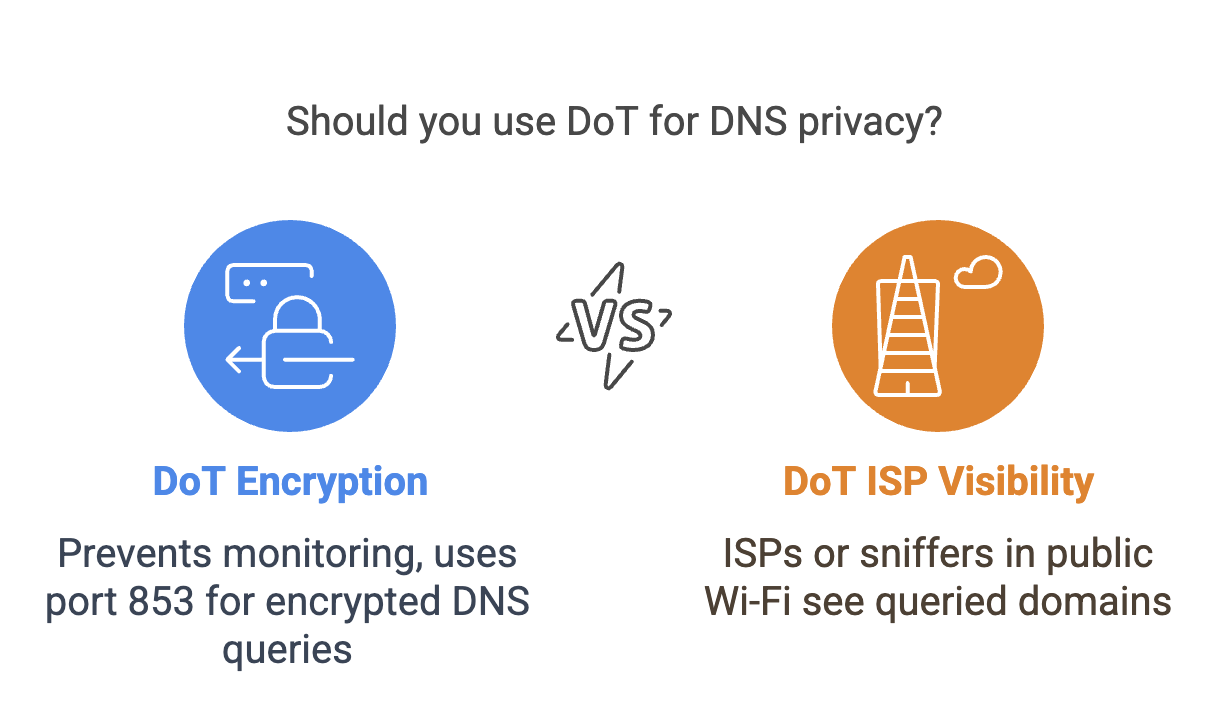
DNS over TLS (DoT) encrypts DNS queries using the Transport Layer Security (TLS) protocol, preventing third parties from monitoring or modifying DNS traffic.
- DoT uses port
853 for secure communication.
- It encrypts DNS queries but still allows ISPs and network operators to see the domains being queried.
- Requires DNS resolvers to support TLS, ensuring privacy for DNS lookups.
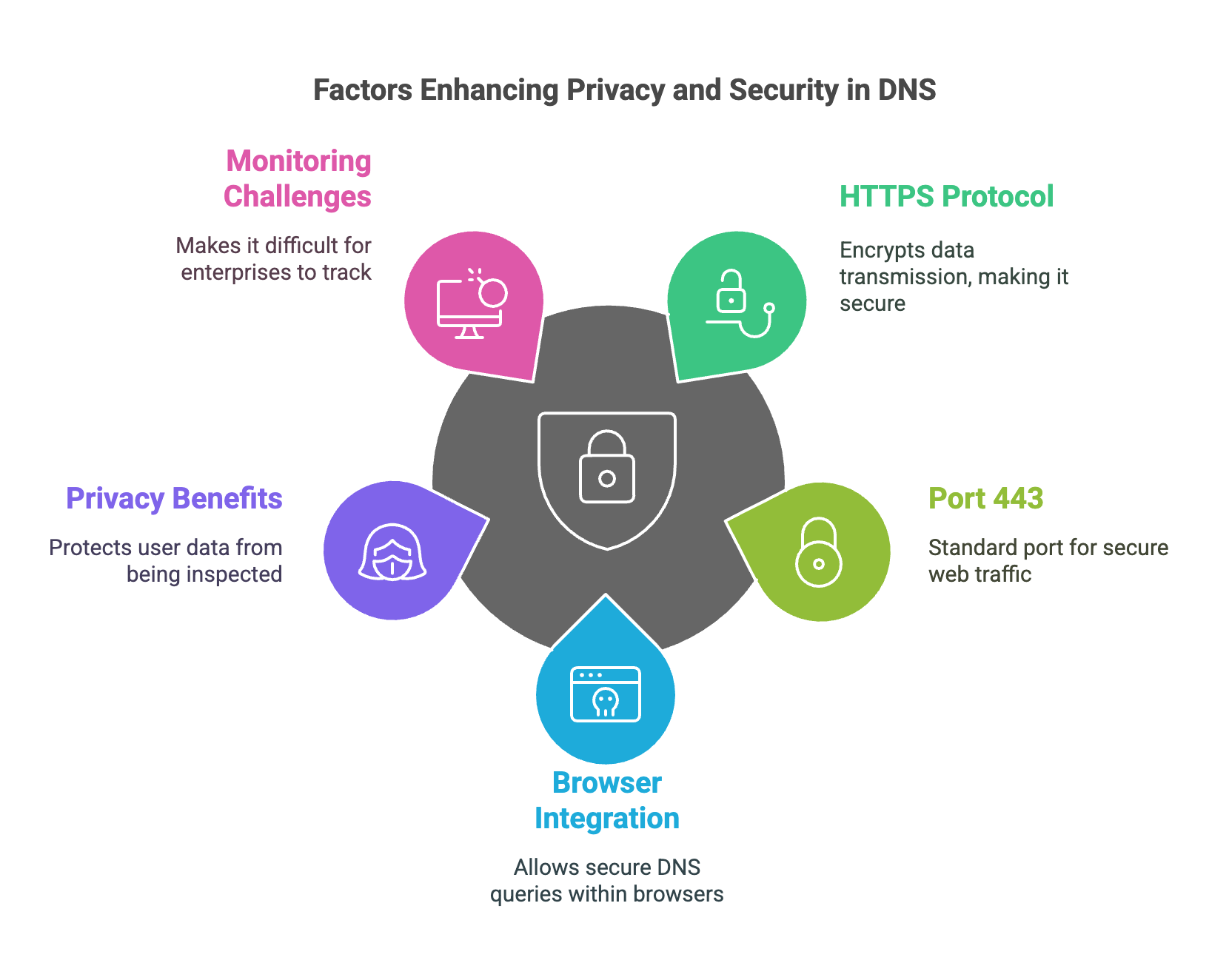
DNS over HTTPS (DoH)
DNS over HTTPS (DoH) performs DNS queries over HTTPS (port 443), making them indistinguishable from regular HTTPS web traffic.
- DoH prevents ISPs and attackers from inspecting DNS queries.
- It enables DNS resolution within web browsers like Firefox and Chrome.
- Offers better privacy but can be harder for enterprises to monitor and filter.
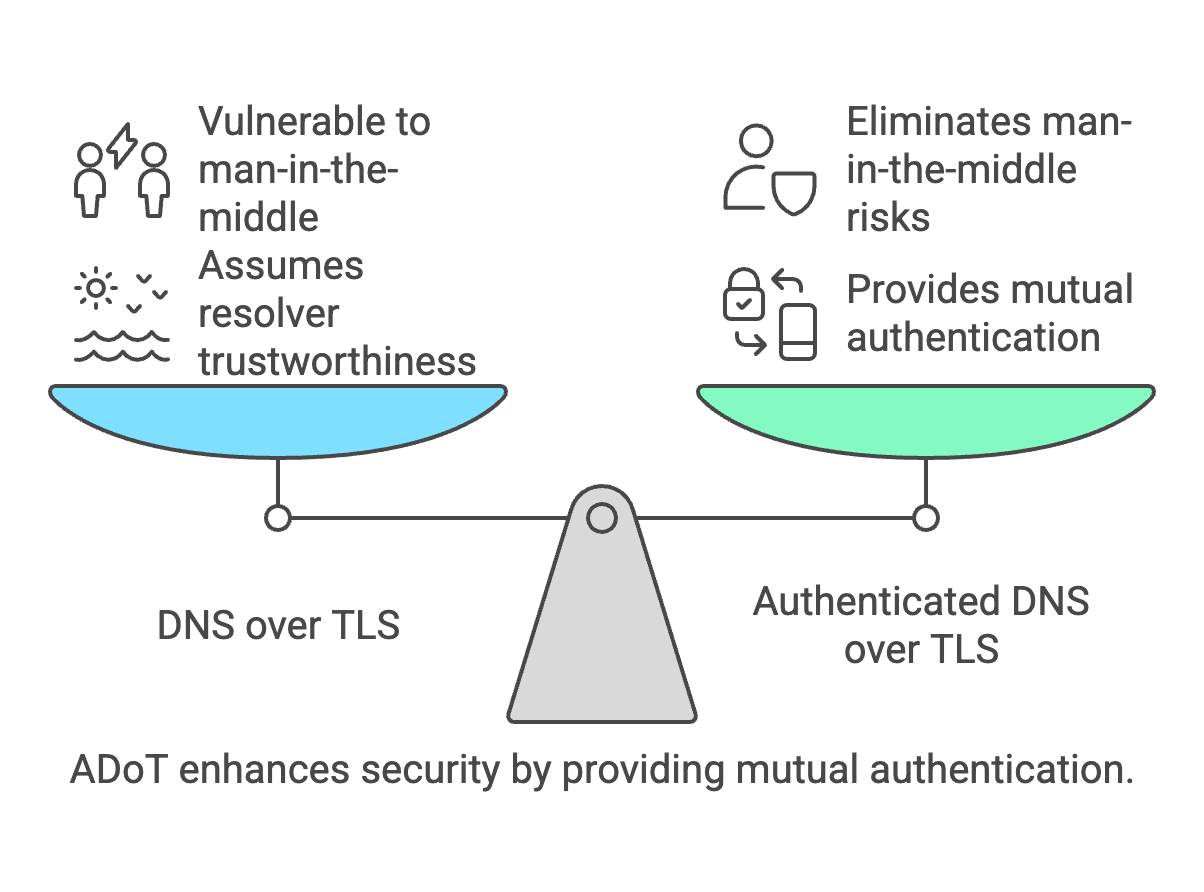
Authenticated DNS over TLS (ADoT)
Authenticated DNS over TLS (ADoT) is an enhancement of DoT, where clients authenticate the DNS resolver before establishing a connection.
- ADoT provides
mutual authentication, ensuring users connect to a trusted DNS resolver.
- Unlike DoT and DoH, which assume the resolver is trustworthy, ADoT eliminates man-in-the-middle risks.
- Particularly useful for enterprise and high-security environments.
Which One Should You Use?
-
Use DNSSEC for integrity (protects against DNS spoofing).
-
Use DoT for encrypted DNS queries while keeping compatibility with traditional resolvers.
-
Use DoH for enhanced privacy and bypassing network filtering.
-
Use ADoT when security and resolver authentication are critical.
By implementing
DNSSEC, DoT, DoH, and ADoT, you can ensure that your DNS infrastructure is
secure, private, and resilient against cyber threats.